It is estimated that between 2.78 and 3.79 million BTC have been lost. This can happen when people forget the password they have set to protect their Bitcoin wallets. Indeed, many of these lost Bitcoins are stuck in wallets created by Multibit Classic – a software that was launched in 2011 and that was abandoned in 2017. Multibit Classic was very popular back then and many people used it to store Bitcoins that they had bought at ridiculously low prices (at least by today’s standards).
However, some of these people are tragically locked out of their wealth as they have lost their password. When they try to access their Multibit Classic wallet, they get errors such as:
- “The wallet password is incorrect”
- “Could not decrypt bytes”
- “Could not decrypt input string”
- “Provided AES key is wrong”
If you are reading this blog post, you probably have tried as many passwords as you could remember, but failed so far. Thankfully, it is possible to automate the process so that you can make more guesses than you ever could by hand. We call this brute forcing. More details below.
Locate the .wallet or .key file to brute force
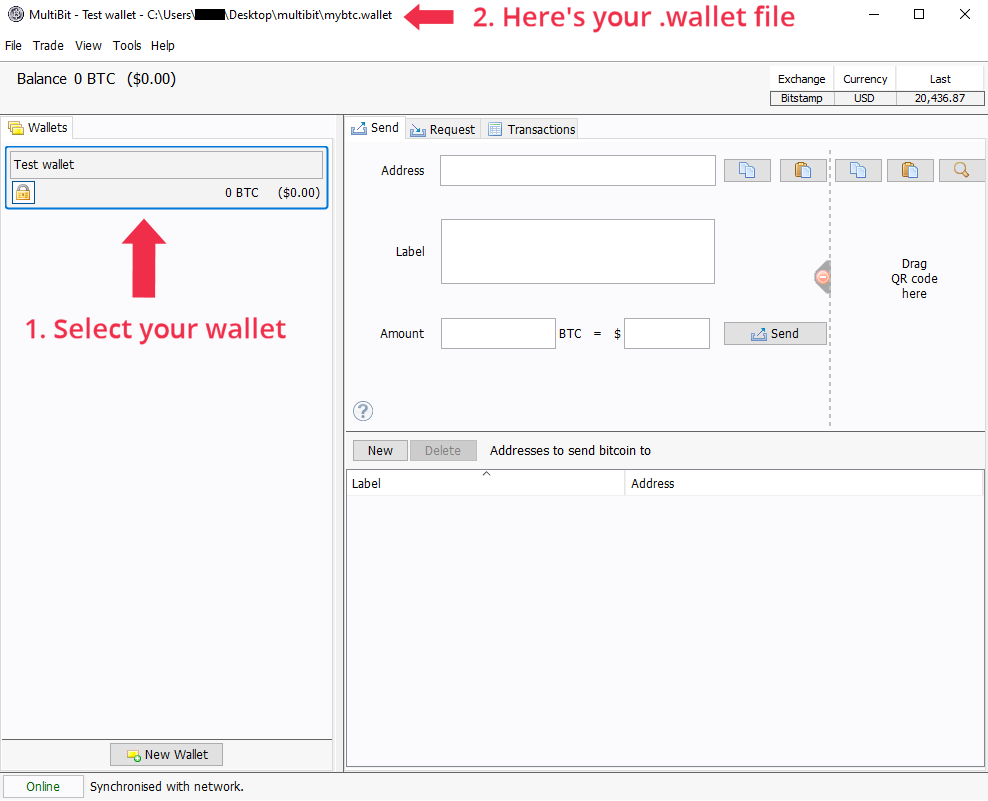
First of all, we have to locate the Multibit file that we are going to brute force. To do so,
open Multibit Classic and select your wallet in the application. In the title bar, you will see the
path to the relevant .wallet file. In this example, my wallet is named mybtc.
While we could mount our brute force attack against the .wallet file directly, we ideally want to
avoid this. The .wallet file is well protected against such attacks and we will be limited to
a few thousands of guesses per second – at most. This is surely better than trying passwords by
hand, but it’s suboptimal compared to brute forcing the .key file associated to your wallet:
depending on the hardware, we can compute millions, if not billions of passwords per second!
The only caveat is that you may not have any .key file.
To find your .key file, go to the path where your .wallet file is supposed to be. There, you should see
a folder that starts with your wallet’s name and ends with -data. In my example, it is named mybtc-data.
Open it. You should now see four folders:
key-backuprolling-backupwallet-backupwallet-unenc-backup
Open the key-backup folder. There should be a file with the following name format: <name of your wallet>-<datetime>.key.
In my example, it is named mybtc-20150615120556.key. This is the file that you are going to brute force.
If you have multiple .key files, it may be a sign that you protected your wallet with different passwords
during its lifetime, though it doesn’t necessarily mean so. It might be worthwhile to try to crack all of them.
If you cannot find any .key file, then you will have to settle for the .wallet file instead.
Crack your password with BTCRecover and hashcat
There are two software that you can use to brute force your wallet: BTCRecover and hashcat. While each one of them has its strengths and weaknesses, they are not so simple that you only have to click on a few buttons and wait for your password to be cracked. In fact, they require you to be somewhat tech savvy. Moreover, you have to be willing to spend hours reading their documentation and searching the web.
I would recommend that you start with BTCRecover as it was designed specifically to crack Bitcoin wallets
and has ample documentation. However, it is the slowest of the two software, especially if you are trying to
brute force a .key file. On the other hand, hashcat is a versatile and powerful tool with a steeper learning
curve and sparser documentation. Speaking of which, if you do use hashcat, you will need the
multibit2john.py
script to convert your .wallet or .key file into a format it can understand.
My service: I recover Multibit Classic wallets
If the above is too complicated, I offer a service where I recover your Multibit password for you. Here’s what you need to know:
- I work exclusively on
.keyfiles. I can check whether you have such a file or not. - I can recover any password that is 7 characters or less. If your password is between 8 and 12 characters, you need to have a fair idea of what you may have used. I’m unlikely to consider your case if you think your password is above 12 characters.
- I will ask you questions to ascertain that you are the rightful owner of the Multibit wallet you want me to crack.
- I charge a 15% fee on the recovered Bitcoins. You don’t have to pay me anything if I don’t succeed.
If you would like to get in touch with me, click on the button below: